Contents
Using a Cisco Router with a Certificate Authority Use the procedure that follows to configure a router to obtain a certificate from your organization's Certificate Authority and use it to secure communications between the router and onePK applications. Navigate to Configuration Remote Access VPN Certificate Management Identity Certificates. Confirm the presence of the Identity certificate. Choose a locate to export the file. Enter the Encryption Passphrase and confirm passphrase. On the new ASA navigate to the same location Configuration Remote Access VPN Certificate Management Identity Certificates. I know you can export the ASA certificate from CLI amd ASDM. Not sure about CA cert though. You might want to check the cert mgmt section on the ASDM. If it is a public CA cert you should be able to download it from cert provider website or just google for it.
Document Overview
Introduction
TLS
Certificates
Phone Authentication
Cisco Unified Communications Manager Authentication
Provisioning Cisco IP phones with LSC Certificates
Using Cisco Unified Communications Manager (with USB Tokens)
Using Cisco ASA Phone Proxy (without USB tokens)
SSL VPN client
IPsec VPN
Conclusion
Appendix
Acknowledgments
References
The majority of Cisco IP phones support secure communication for both control and data channels. The security incorporated into Cisco IP phones includes the encryption and authentication of signaling communications between the Cisco IP phones and the Cisco Unified Communications Manager. Moreover, Cisco Unified Communications Manager supports encryption, authentication, and anti-replay protection of the voice packets exchanged between Cisco IP phones. It is crucial for network administrators to understand the advantages and disadvantages of secure Cisco IP phone communications. This document summarizes the basic security and encryption features that are supported by Cisco IP phones, Cisco Unified Communications Manager servers, and related Cisco voice products. Furthermore, this document is intended to provide best practices for enabling secure encryption frameworks. This document is not intended to provide detailed configuration or feature guides, rather it will present the information to communicate a general understanding of the available options. The intended audience of this document is network administrators, security and voice engineers, and those responsible for managing voice infrastructures. A cursory understanding of basic security, Public Key Infrastructure (PKI), and cryptography principles is required.
VoIP is ubiquitous within enterprise environments. It is widely deployed in enterprises because it is flexible and cost effective. It is critical to secure the transmissions of analog voice that is digitized and transmitted in IP packets. Securing VoIP communication minimizes the risk of theft of private information by a hacker. The scenarios are varied but it is important, for security and compliance reasons, that corporations require secure voice communications utilizing their VoIP infrastructure.
There are several products and end-points involved in a Cisco VoIP deployment, including:
- Cisco IP phones: Endpoints that create and receive calls.
- Cisco Unified Communications Manager: Responsible for provisioning, administering, and monitoring Cisco IP phones.
- Cisco Unified Communications Manager Express: Installed on a Cisco router, this software can be leveraged for Cisco Unified Communications Manager functionality.
- Voice gateways (H.323) and Media Gateway Control Protocol (MGCP): Protocols that interconnect VoIP systems with the analog infrastructure. They are responsible for facilitating calls between IP and analog phones.
The security involved when deploying Cisco Unified Communications Manager Express is similar to a Cisco Unified Communications Manager deployment.
There are many technologies and products that comprise a VoIP system, but for the purpose of discussing security best practices, this document will focus on Cisco IP phones and Cisco Unified Communications Manager.
Figure 1: Typical VoIP deployment with Cisco Unified Communications Manager installed in the Headquarters and Cisco IP phones deployed externally.
To test something in a Lab with another firewall or migrate a whole VPN with certificate to another ASA firewall we have a possibility to migrate the certificate of the firewall to another one. To do it so easily on a Checkpoint firewall will be always just a dream…
The exported data holds the followings:
– private key
– public key (RSA key)
– certificates (ca certificates as well, need to test)
Cisco Asa Import Certificate
| myfirewall01/act/pri(config)# crypto ca export mytrustpoint1 pkcs12 mypassword123Exported pkcs12 follows: —–BEGIN PKCS12—– MIIMlwIBAzCCDFEGCSqGSIb3DQEHAaCCDEIEggw+MIIMOjCCDDYGCSqGAab3DQEH … … MAkGBSsOAwIaBQAEFJ03htn2lF5i8Xw8kXSMWepTflePBBRykjcWlBrSumQneOpl 9ULtbTmhugICBAA= —–END PKCS12—– |
Cisco Asa Export Certificate Form
What if we delete the the trustpoint, we have exported it. Let’s test it:
| myfirewall01/act/pri(config)# no crypto ca trustpoint mytrustpoint1 WARNING: Removing an enrolled trustpoint will destroy all certificates received from the related Certificate Authority.Are you sure you want to do this? [yes/no]: yes INFO: Be sure to ask the CA administrator to revoke your certificates. myfirewall01/act/pri(config)# |
Import it to the another firewall:
First we create a raw trustpoint that will contains the imported trustpoint:
| myfirewall02/act/pri(config)# crypto ca trustpoint mytrustpoint1 myfirewall02/act/pri(config-ca-trustpoint)# exit |
And import the trustpoint in the new firewall:
| myfirewall02/act/pri(config)# crypto ca import mytrustpoint1 pkcs12 mypassword123 Enter the base 64 encoded pkcs12. |
Lets check it out what changed in the config:
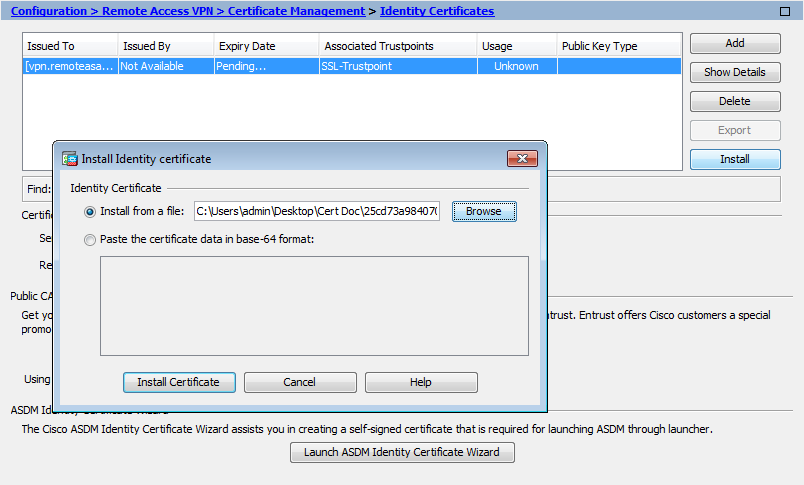
| myfirewall02/act/pri(config)# show run crypto ca trustpoint mytrustpoint1 crypto ca trustpoint mytrustpoint1 keypair ms_cert_key crl configure myfirewall02/act/pri(config)# |
The RSA keypair is updated under the trustpoint.
Cisco Asa Software
| myfirewall02/act/pri(config)# show run crypto ca trustpoint mytrustpoint1 crypto ca trustpoint mytrustpoint1 keypair ms_cert_key crl configure myfirewall02/act/pri(config)# |
Cisco Asa Product Line
That’s it.